-
Duration
60 minutes
-
Medium
Interactive-Video
-
Suitable for
Private User / Employee
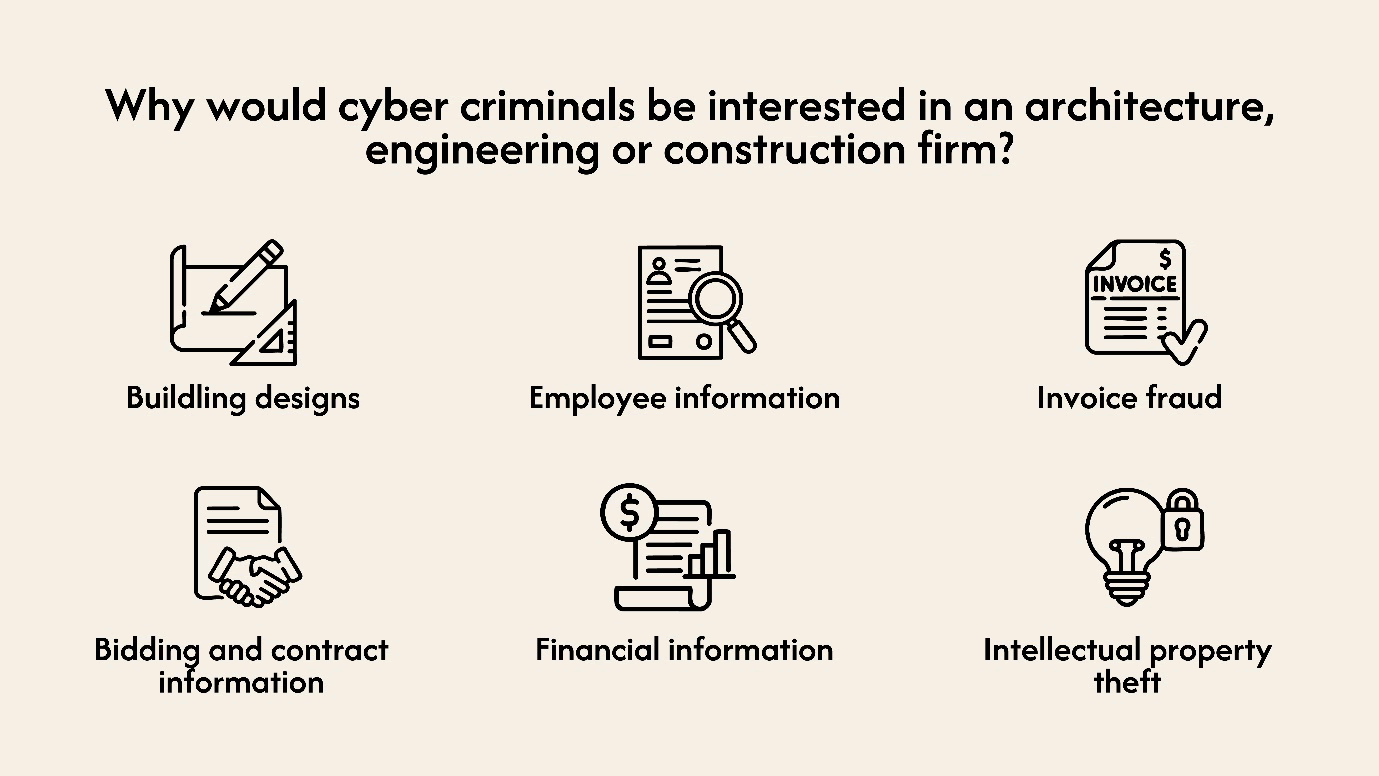
Phishing, ransomware and invoice fraud prevention for the construction industry.
Write your awesome label here.
Phishing awareness training for architecture, engineering and construction firms. A highly customised micro-course with examples of real-world sophisticated cyber threats facing AEC firms in 2025.
Don’t let a near-miss phishing email, WhatsApp, or SMS message become a highly disruptive, financially costly, and reputation-damaging cyber-breach event.
Our interactive training gives your teams the skills to spot, detect, and mitigate sophisticated social-engineering threats facing architecture, engineering, and construction firms. Our phishing awareness micro-course is delivered in plain English by a SANS-certified human risk instructor. Lower your human risk today.
-
How to detect sophisticated phishing emails which bypass your firewall or secure email gateway
-
How to detect fake emails from compromised suppliers
-
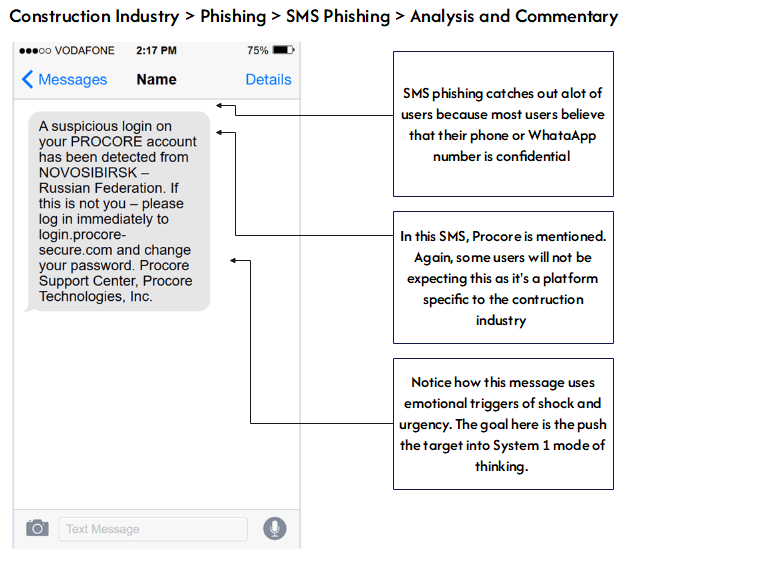
How to detect fraudulent WhatsApp and SMS messages
-
How to detect malware such as ransomware delivered by One Drive, Google Drive, BIM Collaborate, SharePoint and Egnyte
-
How to detect data and credential-stealing malware
-
How to detect fraudulent links purporting to be from services such as AutoDesk and Procore.
-
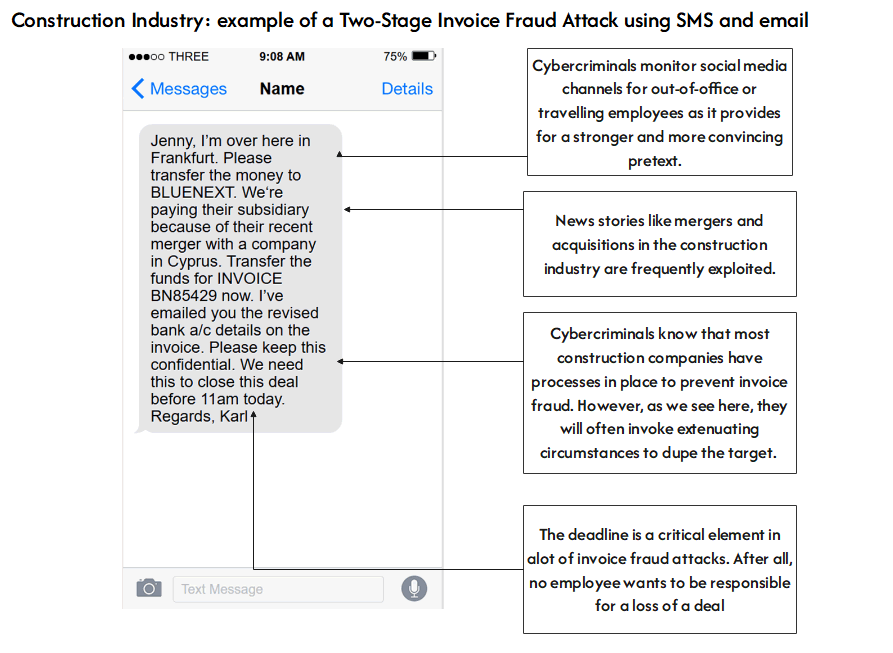
The invoice fraud tricks cyber criminals are using in 2025.
-
A substantial number of ransomware attacks start with phishing emails
Empty space, drag to resize
Contact Us
Empty space, drag to resize
Does any of this sound familiar?
Does any of this sound familiar with your employees?
- A false sense of security: Many of your employees assume that construction, architecture, and engineering firms are not targets for cybercriminals, leaving your organisation vulnerable to attacks. Some of your employees, for example, fail to recognise that crippling effect of a ransomware attack would have on your organisation’s day-to-day operations and future projects.
- Misconceptions about risk exposure: Some of your employees often believe only finance or leadership positions are at risk, overlooking the reality that cybercriminals exploit weaknesses across all roles.
- A history of near-miss incidents: Your organisation has encountered phishing attempts, impersonation schemes, and invoice fraud—fortunately stopped in time. You recognise that reducing the risk of these incidents escalating into full-scale cyberattacks is critical.
- Lack of awareness about impersonation threats: Employees may not fully understand how easily executives, vendors, or clients can be impersonated, leading to unauthorised payments or exposure of sensitive project data.
- Remote work vulnerabilities: Some employees working remotely may lack essential cybersecurity knowledge, increasing the risk of data breaches and unauthorised access.
- Weak password practices: Recycled or weak passwords create easy entry points for attackers to compromise project management platforms like Procore, Autodesk, and Primavera P6.
- Improper data handling: Sensitive information is sometimes stored on unencrypted laptops, which are often left in insecure locations such as company vehicles, heightening the risk of theft, data exposure, and GDPR fines.
- Limited recognition of social engineering attacks: Employees may struggle to identify phishing emails, SMS scams (smishing), WhatsApp fraud, or phone-based deception, making your organisation an easier target.
- Inadequate security awareness training: Your current programme fails to keep pace with evolving threats such as AI-generated scams or multi-stage phishing attacks, leaving employees ill-prepared.
- Overly technical training that fails to engage: Previous security training lacked accessibility, overwhelming employees with jargon instead of equipping them with practical, actionable knowledge.
- Sophisticated deception in collaboration platforms: Your employees have encountered convincing fraudulent links to shared folders on services like Dropbox, OneDrive, and SharePoint, demonstrating the growing sophistication of cyber threats.
- Elevated risk due to third-party breaches: A key stakeholder, such as a materials supplier, has recently suffered a cybersecurity incident, increasing your organisation’s exposure to cascading threats.
- The inevitability of an attack: Without proactive measures, it’s only a matter of time before an employee clicks on a malicious link, triggering a data breach, ransomware attack, or financial fraud. Preventing reputational damage, operational disruption, and financial loss is a top priority.
Benefits
Benefits
Lower your Risk of Operational Downtime
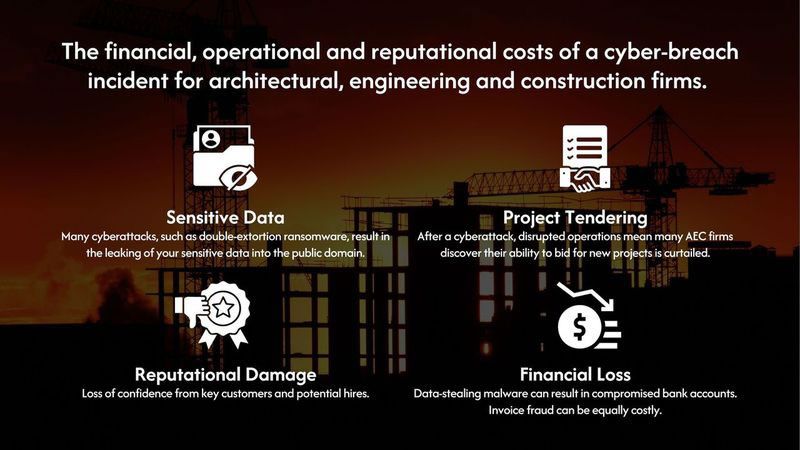
A cyber attack can have a crippling effect on your operations, making essential design, project management and safety documentation inaccessible. All of which, can substantially delay your existing and future projects.
Protect your Sensitive Data
Many cybercriminals now release exfiltrated data into the public domain. Team members trained in phishing awareness are much better placed to protect your contract, planning, employee and financial information.
Lower your Risk of a Ransomware Attack
Many ransomware attacks start with phishing as the initial attack vector. Cybercriminals know that architecture, engineering, and construction firms rely heavily on IT, making them prime targets.
Be Compliant
Be compliant with standards such GDPR, ISO27001, NIS2 and DORA.
A cyber attack can have a crippling effect on your operations, making essential design, project management and safety documentation inaccessible. All of which, can substantially delay your existing and future projects.
Protect your Sensitive Data
Many cybercriminals now release exfiltrated data into the public domain. Team members trained in phishing awareness are much better placed to protect your contract, planning, employee and financial information.
Lower your Risk of a Ransomware Attack
Many ransomware attacks start with phishing as the initial attack vector. Cybercriminals know that architecture, engineering, and construction firms rely heavily on IT, making them prime targets.
Be Compliant
Be compliant with standards such GDPR, ISO27001, NIS2 and DORA.
Who is this micro-course suitable for?
Who is this micro-course suitable for?
This course is designed for anyone who works in construction, engineering or architecture firms. These include: construction managers, site supervisors, quantity surveyors, project estimators, project managers, site inspectors, BIM modellers, operations managers, office managers, architects, financial assistants, administrative assistants, civil engineers, business development teams and contractors.
We educate your employees on the telltale signs of a phishing email, SMS or WhatsApp.
How can architecture, engineering and construction firms lower their cyberattack risk?
How can architecture, engineering and construction firms lower their cyberattack risk?
Enable Multi-Factor Authentication—not just on email accounts but also on BIM Connect, email marketing applications, cloud storage services, and, of course, password managers.
Perform regular backups—Create frequent backups of local machines or VMs. Make sure that some backups are air-gapped from your network. Ransomware groups often program their ransomware software to encrypt or delete your backups.
Keep devices, operating systems, and applications up-to-date. Patch them as soon as an update is released.
Perform network monitoring - Use a tool like Palo Alto Cortex to monitor suspicious connections.
Use robust passwords. Robust passwords can thwart brute-forcing attacks for initial entry, making it more difficult for hackers to move laterally across your network.
Enable Google Drive data loss prevention—Most organisations forget this preventative measure. By enabling Google Drive's data loss prevention feature, you can help prevent sensitive data from leaving your organisation via shared links.
End-user security awareness training—Security awareness is essential. Many phishing campaigns bypass secure email gateways and end-point detection software. And it’s not just about email. Cybercriminals now extensively use SMS, WhatsApp, and even old-fashioned telephone calls to socially engineer your team. Moreover, your users look after credentials, which are the keys to your network or email system. Your users are the last line of defence. They are your greatest asset in defending your organisation—security awareness is perhaps one of the most significant investments you will ever make.
Perform regular backups—Create frequent backups of local machines or VMs. Make sure that some backups are air-gapped from your network. Ransomware groups often program their ransomware software to encrypt or delete your backups.
Keep devices, operating systems, and applications up-to-date. Patch them as soon as an update is released.
Perform network monitoring - Use a tool like Palo Alto Cortex to monitor suspicious connections.
Use robust passwords. Robust passwords can thwart brute-forcing attacks for initial entry, making it more difficult for hackers to move laterally across your network.
Enable Google Drive data loss prevention—Most organisations forget this preventative measure. By enabling Google Drive's data loss prevention feature, you can help prevent sensitive data from leaving your organisation via shared links.
End-user security awareness training—Security awareness is essential. Many phishing campaigns bypass secure email gateways and end-point detection software. And it’s not just about email. Cybercriminals now extensively use SMS, WhatsApp, and even old-fashioned telephone calls to socially engineer your team. Moreover, your users look after credentials, which are the keys to your network or email system. Your users are the last line of defence. They are your greatest asset in defending your organisation—security awareness is perhaps one of the most significant investments you will ever make.
How supply chain attacks work in the architecture, engineering and construction sectors.
How supply chain attacks work in the architecture, engineering and construction sectors.
SecureClick recently encountered a rather unfortunate case of a consulting engineering firm that lost a rather lucrative business contract due to a supply chain attack. What happened? One of their employees got “phished.” A cybercriminal sent them a SharePoint file containing data-stealing malware that captured their email account password. The cybercriminal gained control of the employee’s email account. This hijacked email account was then used to propagate ransomware to other firms and individuals in their M365 global address book. Unfortunately, a construction company (with which the mechanical engineering firm had a long-standing and lucrative relationship) fell prey to the attack. One of their employees believed that because the email was from a trusted source, its attachment was safe to open. With numerous systems (servers, PCs and laptops) maliciously encrypted, the construction firms' operations were significantly curtailed by this incident. The event soured the relationship between the two firms. After years of project cooperation, the construction selected a different engineering firm some months later.
Sample Training
Sample Training
The power of scenario-based training reflecting real-life 2025 cyber threats. Immersive learning that keeps learners genuinely captivated and teaches lessons that stick.

At SecureClick, we bring cybersecurity awareness to life with an engaging narrative—no cartoons, no cheesy voiceovers. Why does this work? People forget isolated chunks of information security facts. People remember information when it is put in the context of stories. This means, your employees will remember what they saw or heard when facing a real-life security decision.
Atlantic Point Construction and Consulting Engineers is a fictitious company. However, the threats it faces are based on real-life threats targeting the construction industry in 2025.
Atlantic Point Construction and Consulting Engineers is a fictitious company. However, the threats it faces are based on real-life threats targeting the construction industry in 2025.
Mythbusting
Mythbusting
Dispelling user misconceptions about information security is fundamental to effective security awareness training. Over the years, SecureClick has spoken to dozens of hacking victims, and the same security misconceptions keep reappearing. These misconceptions must be addressed because beliefs and attitudes are strongly correlated to behaviours. In our interactive training, using plain English, we dispel these misconceptions with clear explanations and real-life examples, substantially lowering your organisation's human IT risk.


Scenarios
Scenarios
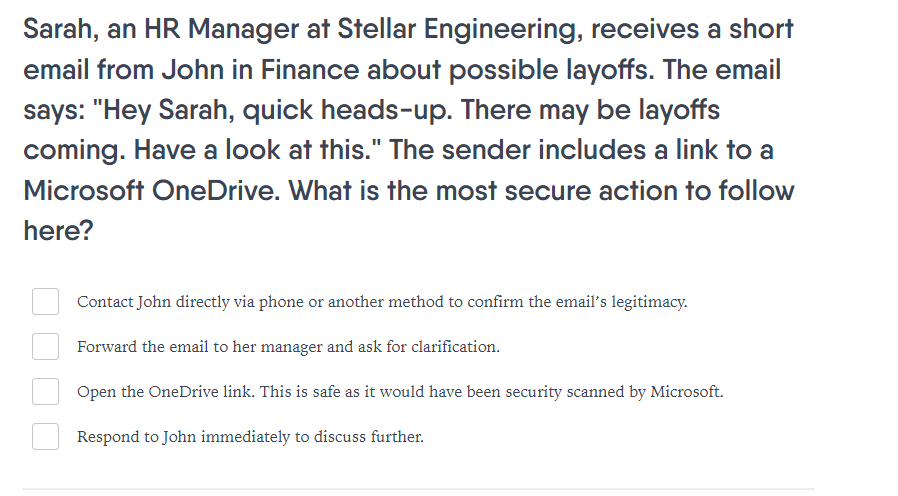
We use realistic cyber threat scenarios to test your team's response to threats like nuanced phishing emails. These emails are not typically used in generic off-the-shelf phish-awareness applications, which leaves your employees vulnerable.
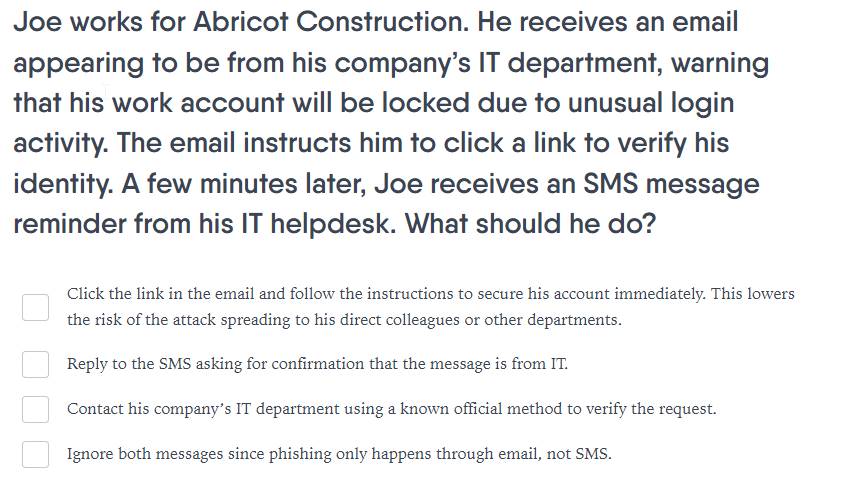
Account Takeover / Internal Phishing Scenarios
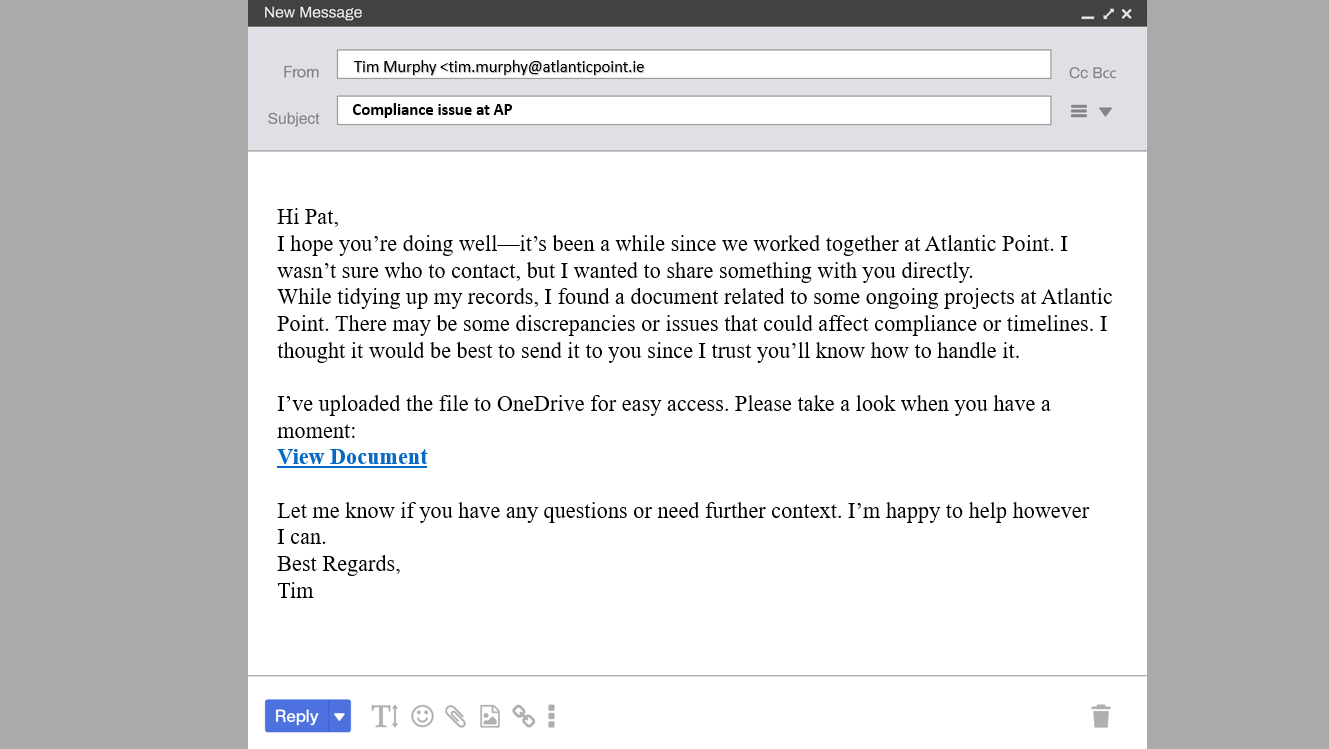
This email is designed to test how your employees would respond to an internal phishing attack. This occurs when the sender is known to the recipient. Here, the cybercriminal is using a hijacked email account of an ex-Atlantic Point employee and impersonating the employee. This type of email is dangerous because it will bypass controls such as secure email gateways. Your employees are the last line of defence here. This email is designed to test whether they can identify a phishing email (even though it’s from a known sender and known email address) and test their reaction to a “curiosity lure” – in this case, a link to a SharePoint file.
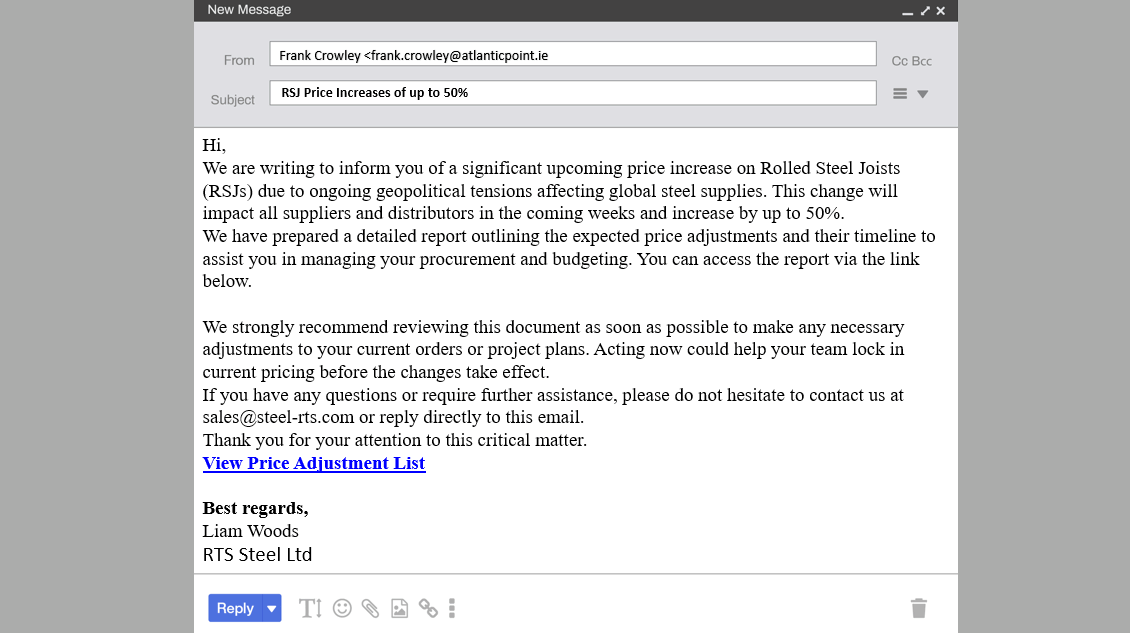
In recent years, malspam campaigns have become a favourite of cybercriminal groups propagating ransomware. These often work because many users erroneously believe that commercial email messages (or marketing) in nature must be safe to open. In reality, links or attachments purporting to be pricelists or brochures can be conduits for data or credential-stealing malware.
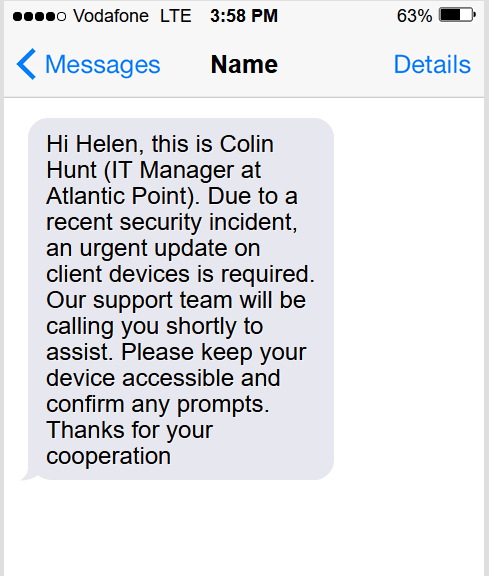
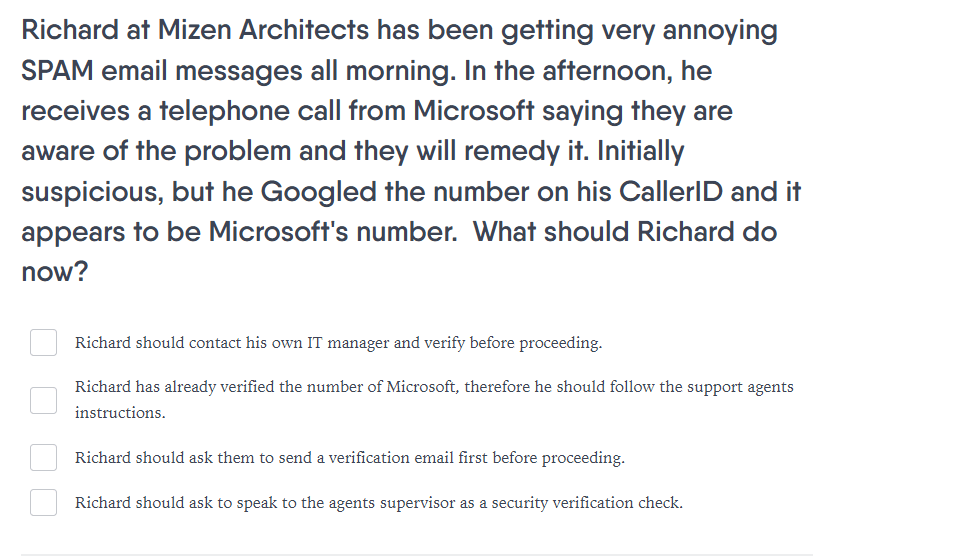
Cybercriminals impersonating IT staff is a common problem. This is especially true for new hires (cybercriminals often being keen monitors of LinkedIn) unfamiliar with their new workplace's systems and protocols. A message like this will also catch users because some users are still unfamiliar with Caller ID spoofing techniques.
This email tests how employees react to an “internal phishing” email. The sample scenario above uses a credible pretext and a reasonably strong curiosity lure. In our interactive training, many employees will admit to opening such an email, especially if the sender's email address appears valid. Cybercriminals commonly use this type of email, especially when an ex-employee's email account has not been adequately revoked. The OneDrive link will either lead to a credential-stealing portal set up by the cyber-criminal or result in the user inadvertently downloading data-stealing malware. This can culminate in data exfiltration, invoice fraud or ransomware.
This email tests how employees react to an “internal phishing” email. The sample scenario above uses a credible pretext and a reasonably strong curiosity lure. In our interactive training, many employees will admit to opening such an email, especially if the sender's email address appears valid. Cybercriminals commonly use this type of email, especially when an ex-employee's email account has not been adequately revoked. The OneDrive link will either lead to a credential-stealing portal set up by the cyber-criminal or result in the user inadvertently downloading data-stealing malware. This can culminate in data exfiltration, invoice fraud or ransomware.
Case Study
Case Study
How a Dublin-based consulting engineering firm made its team more resilient against phishing and impersonation attacks.
Our client, a consulting engineering firm that designs vital facilities such as wastewater management systems for local authorities across Ireland wanted to lower its human IT risk.
Challenge:
Several of their UK and European peer organisations experienced ransomware and sophisticated invoice fraud attacks. As a digital-first firm, much of their work was now performed on Cloud-based platforms (such as Autodesk and Office 365), and they were concerned about the effects of a cyber-breach event on their operations and reputation. They recognised that their main clients (local authorities) were concerned about supply chain attacks. Just one of their firm’s email accounts getting hijacked could result in the exposure of confidential information and the compromise of a local authority client. They also realised that such a cyber-breach event could seriously jeopardise future business relations.
Concerns
The firm received some very “obvious” phishing emails, SMS and WhatsApp messages. However, not all of these communications were that obvious. Some of these messages referenced specific staff members and some impersonated software vendors (such as AutoDesk and Procore). For example, on one occasion, an employee got a message followed up by a WhatsApp message purporting to be from the CEO about a payment transfer. Even more worrying was that none of these communications was flagged by their email gateway or the in-built detection tools of their Microsoft 365 collaboration platform. They were aware that even if one of these malicious communications was successful, it could lead to a crippling ransomware attack which would delay current and future projects. Not only would such an incident damage their reputation and result in sensitive data being potentially exposed, but delayed projects would not be long in negatively impacting on cashflows.
Approach
We liaised with their in-house IT team to investigate any further threats they experienced. Our threat assessment revealed that ransomware, data exfiltration and business email compromise were their most significant threats. The vectors for these attacks were primarily email, text messaging and vishing (telephone-based social engineering)
Training
Using our Human Cyber Risk Susceptibility Survey (HCRSS), we first determined their employees' underlying cyber risk attitudes and beliefs. The results of which revealed some interesting findings.
1) Over 43% of employees believed that threat actors would not target them but rather their colleagues in the finance department or boardroom instead.
2) Over 68% of their employees reported that communications (such as email and SMS) from cloud-based platforms such as Microsoft 365 were “very secure”. Many employees believed threat actors would find it difficult to impersonate due to Microsoft's security controls.
3) Over 55% of their employees believed emails from colleagues or suppliers are “very safe when you know the sender”.
The results were concerning. Their employees held some IT security misconceptions, which left their firm vulnerable. First and foremost was the issue of cyber threats and a lack of relevancy. It was perfectly understandable why employees in some departments believed they would not be a target for cybercriminals. However, we showed them how “lateral movement” works during our training using real-life case studies. We showed them how just one compromised email account can result in a cybercriminal reaching the master switch (domain controller) of their network and enabling data exfiltration and ransomware attacks.
Their employees also placed a lot of trust in notifications from cloud collaboration platforms such as Microsoft 365 and AutoDesk. In so-called “Living off the Land” (LOTL) attacks, cybercriminals commonly exploit services such as Forms, OneDrive, SharePoint and BIM360 to steal credentials and propagate malware. We deconstructed some real-life Lotl attacks to show their employees how easily these “trusted” services can be exploited. We showed them how threat actors can exploit the trust of services such as OneDrive, MS Forms, SharePoint and DocuSign to propagate data-stealing malware and facilitate credential theft.
Internal phishing and account takeover (ATO) attacks pose a significant problem for firms in the AEC sector. A study from IBM found that up to 40% of phishing attacks now involve “internal phishing”. However, our survey found that a significant cohort of this consulting engineering firm’s employees believed that emails from known senders were “very safe”. We showed employees the fundamentals of such attacks and real-life case studies of how employees in peer firms got caught out.
Putting their Cyber Security Learnings into Practice
A vital part of our Human DTECTR training system is knowledge transfer and getting participants to apply what they have learned to real-life scenarios actively. For this, we used our CyberGame. During this tabletop exercise, employees assume the role of hackers. Using Zoom's breakout rooms feature, participants were broken into teams. Each team was given the name of a fictitious consulting engineering firm and told to hack them using social engineering. Participants received prompt sheets with various attack mechanisms (simplified) and social engineering pretexts. This brings learning to life and gets employees thinking about the multi-threaded techniques which treats actors use in real-life attacks, which is often difficult to convey over e-learning platforms.
Results
Our post-training Human Risk Cyber Susceptibility Survey results reveal a demonstrative improvement in employee resilience. Only 12% of employees believed they would not be a cybercriminals target. 23% of employees now reported cloud-based platforms such as Microsoft 365 as “very secure.”. 14% believed emails from colleagues or suppliers are “totally safe because I know the sender.” Furthermore, their internal IT team noticed that employees were much more likely to report suspicious incidents. This reporting of suspicious incidents increased from just 12% to 29%. The firm’s management could now prove to their key customers concerned about supply-chain attacks that their team had undergone security awareness training, giving them confidence for future business cooperation. Knowing that their employees now had a greater sense of accountability and were better able to spot threats, which evaded their technical defences allowed their IT teams and management to sleep a little sounder at night.
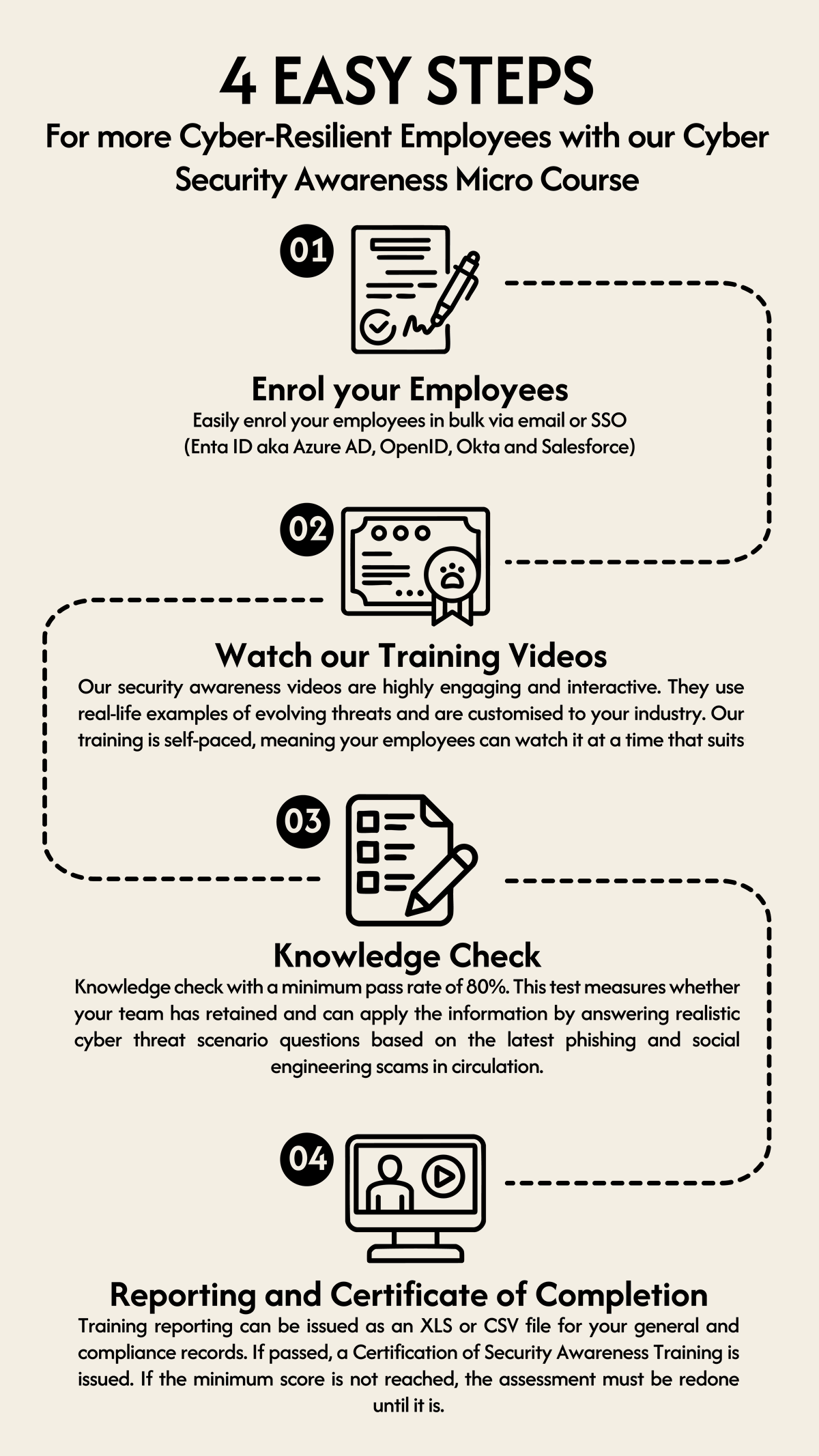
Sample Knowledge Check
Sample Knowledge Check
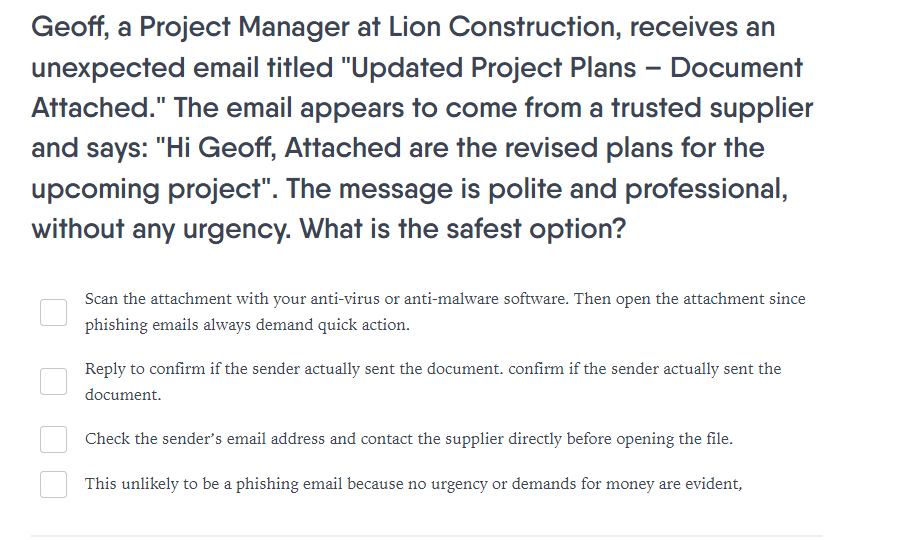
Accordion Description
Empty space, drag to resize

Empty space, drag to resize
Empty space, drag to resize
Before Training
-
Struggles to recognise phishing and impersonation attempts
-
Under-estimates the sophistication of cyber criminals in 2025
-
Their risk radar of threats is narrow in scope.
-
Believes that end-point protection software is a catch-all.
-
Clicks on suspicious links without hesitation.
-
Responds impulsively to urgent messages.
-
Unclear how to handle phishing attempts.
-
Increases risk of data breaches.
After Training
-
Confidently identifies phishing and impersonation attempts.
-
Understand the sophistication of cyber criminals in 2025
-
Their risk radar is broad in scope.
-
Understand the inherent weaknesses of end-point protection software.
-
Evaluate email content before clicking.
-
Applies critical thinking to detect manipulation.
-
Follows a clear process for reporting phishing attempts.
-
Helps reduce organisational security risks.
Very Informative
Very informative, interactive & interesting
Participant
Recommended
I organised on online training session with SecureClick. Our eyes were opened by what we learned from Robert, and we were able to overhaul our safety practices straight away with what we’d picked up. The session was really informative and engaging, and touched on everything we wanted it to. It was also well tailored to suit the needs of our organisation. I’d advise any organisations who have concerns about their IT security to book a session with SecureClick
CEO, Cultural Exchange Association, Belfast
Very Helpful
We engaged SecureClick to run some instructor-led training for our team. The training content was well delivered, engaging, interactive and was tailored to the business domain in which we operate. The overall feedback from employees was very positive. It got them thinking about some social-engineering blind spots which we had not considered before. This is a very worthwhile training session
Compliance Officer, Software Development Company, Dublin
Write your awesome label here.
Created and Hosted by
Robert Scanlon B.Sc SSAP
Human Risk Instructor
A SANS-certified human risk instructor who believes that great learning starts with learner engagement, relevant content and interactivity.

We’re passionate about IT security. But we’re also passionate about studying and altering human behavior when it comes to information security. Because, let’s face it, most IT security threats these days are designed exploit poor end-user security behaviours.
Useful Links
Contact Details
-
info@itsecurityawareness.ie
-
+353 1 687 5795
-
Tara Suite, 7 Trinity Street, Dublin 2, Ireland.


Copyright © 2025

